I sure don’t feel safe just ignoring it, considering the frequency.
It is actually safe to ignore them. It means either someone has an email address similar to yours, or a bot of some sort has you email address and only your email address.
Essentially, someone or something goes to the login screen, enters your login, and says “I don’t have the password, let me in!”.
Sending a code to your email like this is the first step in letting someone in without the password, or more specifically to having them reset it.Since the email is to check “did you ask for this?”, doing nothing tells them that you did not.
If you want some extra peace of mind: https://account.live.com/Activity should show you any recent login activity which you can use to confirm that no one has gotten in.
Also, use two factor, a password manager, and keep your recovery codes somewhere safe. The usual security person mantra. :)
This is all good information and seems well intentioned, but it’s worth pointing out in a post about account security that clicking links provided by others and giving it your login information is very unwise (even/especially links in emails like these). For the link you provided, it’d be better to recommend going through a primary microsoft page or login that can be confirmed by the user and getting to the activity history page from there
Also, use two factor, a password manager, and keep your recovery codes somewhere safe. The usual security person mantr
Well, I found the recent activity and none of these were me. At least they all appear to say Unsuccessful sign-in.
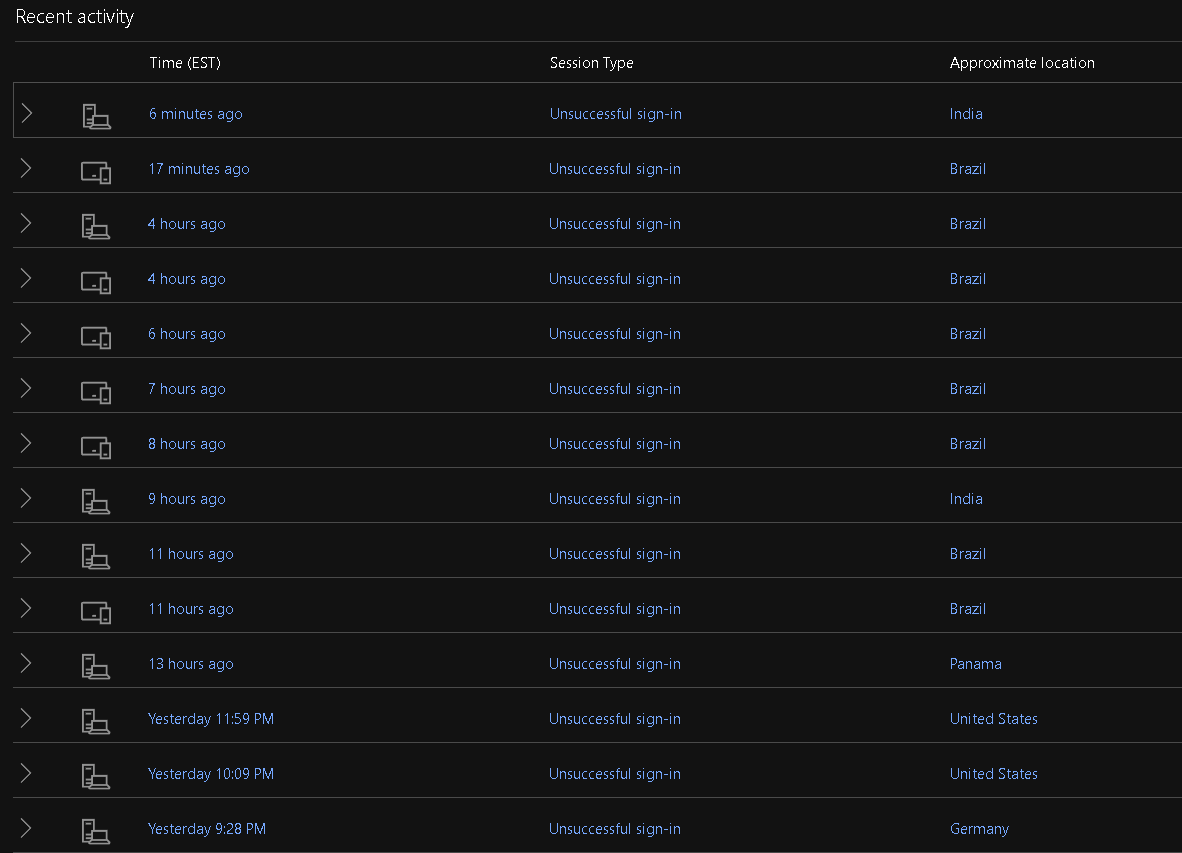
Yup, that would indicate that likely a bot is trying to guess it’s way in.
You are still safe.
The only weird thing here is that Microsoft lets such things bother you instead of guessing that you didn’t teleport to Brazil and instead putting a little extra burden on the Brazil end before sending you an email.
If you’re still feeling worried, the biggest thing you can do is enable two-factor auth (which you should do anyway), or even better: enable something like passkeys which are very secure and also easier than username/password.
Two-factor/password manager is the “remember to brush and floss” of the security industry, so… Please do those things. :)
You can create an email alias for your Microsoft account and then only enable login from that account. If you then do not use that email for anything but the login, you should be pretty safe from credential stuffing attacks.
I had a very similar issue with multiple failed login attempts and changing my login email stopped it right away.
Change your password immediately to something you’ve never used before and isn’t similar to current passwords. If you’re getting random 2fa codes, someone is able to complete your first factor, so fix that ASAP.
It might not be 2-factor. Microsoft has an option to log in via email code, which doesn’t need a password.
Use Microsoft authenticator on your account, it won’t stop people from trying to access your account but you’ll stop getting these and it’s generally safer than any kind of email based 2fa
deleted by creator
The message is multi-factor
Oh, I missed that in the gutter of the message.
This is a common attack tactic, then, called MFA Fatigue. It also means they probably have Ops password already. Or Ops service provider is doing something dumb. (MFA requests shouldn’t be sent out without the other factor being known.)Edit: There’s no approve link there. Just ignore these. If you got a lot of these, do setup MFA.
It’s not mfa fatigue. MS sends a code to the email. There is no accept or deny in the email.
It’s common for people to get these when their email address is similar to my dad’s and he forgets his password again.
Part of my concern is the email has part of an uncommon spelling of name + some numbers. And that it started all of a sudden, every day. The email is several years old and only now it’s begun happening every day.
I hope you’ve turned on 2FA.
Change your password to a randomly generated password and them setup 2FA
Do not click on anything in the emails as they may be phishing attempts
Just to be clear, change your password by manually typing in the address of the service in question.
Do not use the link in the email to navigate to the service for password changing.
I got one of these emails. It isn’t even MFA, nothing to reply with the code to. It doesn’t even say which Microsoft account, it sent it to my GMail recovery account. It’s so utterly bad not being able to trace the attempt to its source. It’s sus that I’m not the only one to have recently experienced this out of nowhere. Maybe it’s an attempt to farm valid Microsoft emails from the way this service behaves?
If it happened on a MS account you have, you can check the activity part of the account, it should list all login attempts and give you an IP for each.






